FortiGate FortiOS
This section contains an example configuration for Fortinet. It may differ according to the Fortinet framework version. This document was created according to Fortinet 200D Firmware v6.0.3 build0200 (GA).
Radius Settings
- First of all, Wirofy server must be added via User & Device > RADIUS Servers.
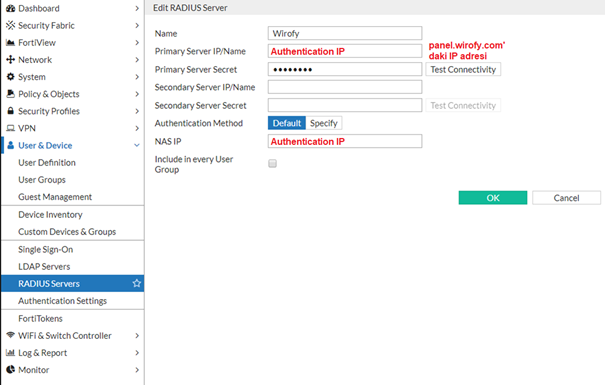
- To customize the Radius Port, XXXX must be defined as the Authentication port in the Wirofy panel. The following commands should be run on the Fortigate console.
config system global
set radius-port XXXX
end
Instead of XXXX, the authentication port value in the device details in the wirofy panel should be written. {.is-info}
Firewall Settings
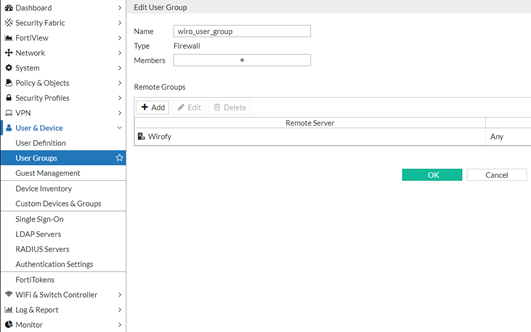
In the User & Device > User Groups section, the user group should be created by selecting the Wirofy radius server defined in the upper step of the Firewall type.
Https forwarding can be turned off by running the following command on the Fortinet CLI screen (SSH or management panel cli). SSL does not give certificate errors for requests starting with traffic.
config user setting
set auth-secure-http disable
end
SSID & Interface Settings
The wireless network to be applied to hotspot is created via WiFi & Switch Controller> SSID. If it is to be implemented directly over the internet, you should proceed with Network> Interfaces. The relevant Vlan and Interface are organized. Subnet ranges and Dhcp are regulated on demand.
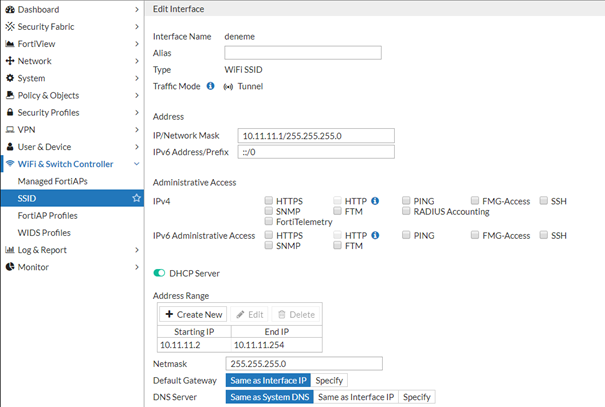
In the Wifi Settings section, External should be selected as Authentication Portal and the value should be Login Page Url (https://connect.wirofy.com/login/XXXXXXXX\) in the device detail in the Wirofy account. Wirofygroup added in User groups will be selected as UserGroups. The address to be redirected after successful entry to Redirect after Captive Portal is written.
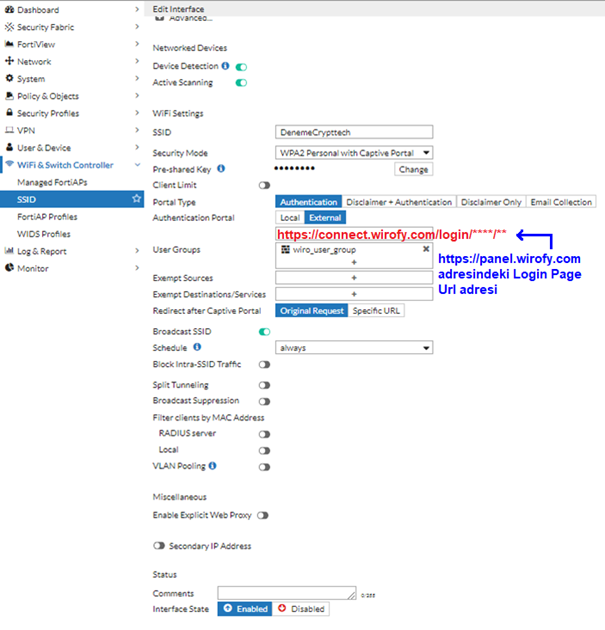
Walled Garden Settings
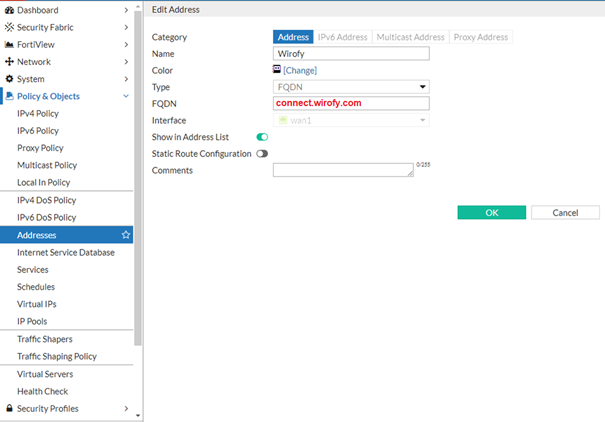
An object is created for the Authentication IP address (or FQDN connect.wirofy.com) in your Panel Wirofy Account via Policy & Objects > Addresses to define relevant access policies.
From Policy & Objects> Policy> IPv4 page, Wirofy.com, the Walled Garden, is granted the necessary access permissions. Access is required without authorization.
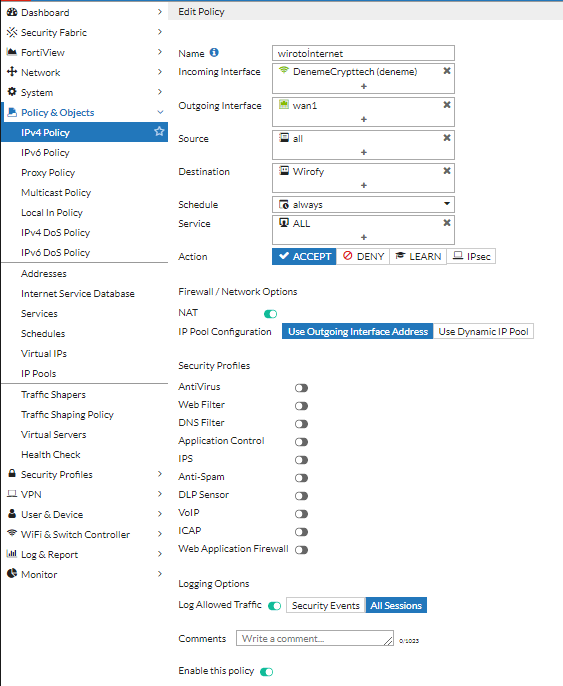
For the added policy, the following command should be entered via CLI. The policy_id value can be found in the policies section.
config firewall policy
edit <policy_id>
set captive-portal-exempt enable
end
end
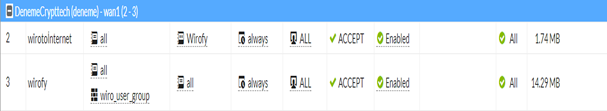
Internet access is provided to authorized users by the following description from the Policy & Objects > Policy > IPv4 page. The total of added rules should be as follows.